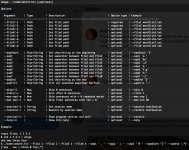
Utility "raw2dyna" (included in the John the Ripper package)
┌──(freeroute㉿Orion-Nebula)-[/usr/local/src/john/run]
└─$ ./raw2dyna --h
usage ./raw2dyna [options] < input > output
Options:
-d=# dyna number (-d=12 and $dynamic_12$hash$salt is used)
-a ALL hashes get $HEX$ and not simply hashes which have problems
-ls=# The salt is the leading data, and it is # bytes long
-ss=b The salt separator char is b a blank -ss= means no separator char
-hl=n The length of hash. SHA1 is 40, MD4/5 is 32, SHA256 is 64, etc
-2h=r perform a simple convert to hex. the string r is converted to $HEX$hhhh...
-2r=h perform a simple convert out of hex. the hex string h is converted to raw data
if either -2h or -2r are used, then the convert is done and the program exits
defaults are -d=12 -ss=: -hl=32
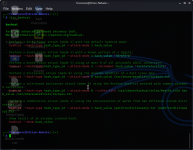
To convert any string to hexadecimal, use the -2h option:
└─$ ./raw2dyna -2h='Orion' 1 ⨯
$HEX$4f72696f6e
To convert hexadecimal string to raw data, use -2r option:
└─$ ./raw2dyna -2r='4f72696f6e'
Orion
┌──(freeroute㉿Orion-Nebula)-[/usr/local/src/john/run]
└─$ ./raw2dyna --h
usage ./raw2dyna [options] < input > output
Options:
-d=# dyna number (-d=12 and $dynamic_12$hash$salt is used)
-a ALL hashes get $HEX$ and not simply hashes which have problems
-ls=# The salt is the leading data, and it is # bytes long
-ss=b The salt separator char is b a blank -ss= means no separator char
-hl=n The length of hash. SHA1 is 40, MD4/5 is 32, SHA256 is 64, etc
-2h=r perform a simple convert to hex. the string r is converted to $HEX$hhhh...
-2r=h perform a simple convert out of hex. the hex string h is converted to raw data
if either -2h or -2r are used, then the convert is done and the program exits
defaults are -d=12 -ss=: -hl=32
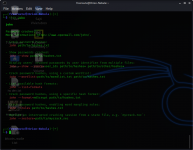
To convert any string to hexadecimal, use the -2h option:
└─$ ./raw2dyna -2h='Orion' 1 ⨯
$HEX$4f72696f6e
To convert hexadecimal string to raw data, use -2r option:
└─$ ./raw2dyna -2r='4f72696f6e'
Orion