SpaceCowboy
Active member
Hello everyone
i was wondering if someone can find the algo for this router
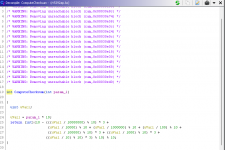
i uploaded the lib directory from the firmware and the photo contains the default wpa key which is 13 length hex and admin password is [A-Z0-9] 10 characters
thank you
i was wondering if someone can find the algo for this router
i uploaded the lib directory from the firmware and the photo contains the default wpa key which is 13 length hex and admin password is [A-Z0-9] 10 characters
thank you